Jump To Section:
WP File Manager Plugin, a free WordPress plugin available on the WordPress plugin directory, became the latest victim in a series of ongoing hacking attacks. The purpose of the plugin is to manage files throughout your server that you may not previously would have been able to edit or access solely from your WordPress installation.
A key examples where the WP File Manager really comes in handy is if you require uploading a HTML verification file to your server in order to verify your own domain.
How many websites were affected?
WP File Manager was a huge hit among the WordPress community and as such was installed by over 700,000 websites according to WordPress' plugin repository.
From the subsequent attacks, the plugin has suffered around a third of all its previous installations; reducing the total installations to just under 500,000 with more uninstalls likely to occur during the coming days, weeks and months.
Lowerbeforwarden Virus
The popular WordPress plugin WP File Manager was hacked by a zero day exploit that installed a script on the website to show ads to website traffic of infected websites in order to generate profit for the malicious creator.
From a security aspect, what concerns us most is the amount of native WordPress files that the virus looks for and exploits including the standard plugin Hello Dolly and WordPress's configuration file, wp-config.php.
The system also performed a series of requests to external websites to download and extract various .zip folders depending on which WordPress installation was active.
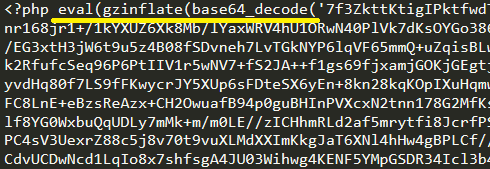
The coding languages used throughout this attack consisted of a mixture of JavaScript and PHP. The malicious code used a combination of encryption techniques to hide the server from detecting malicious code including:
- Base64 decode
- gzinflate
- Eval
- btao
Backdoor
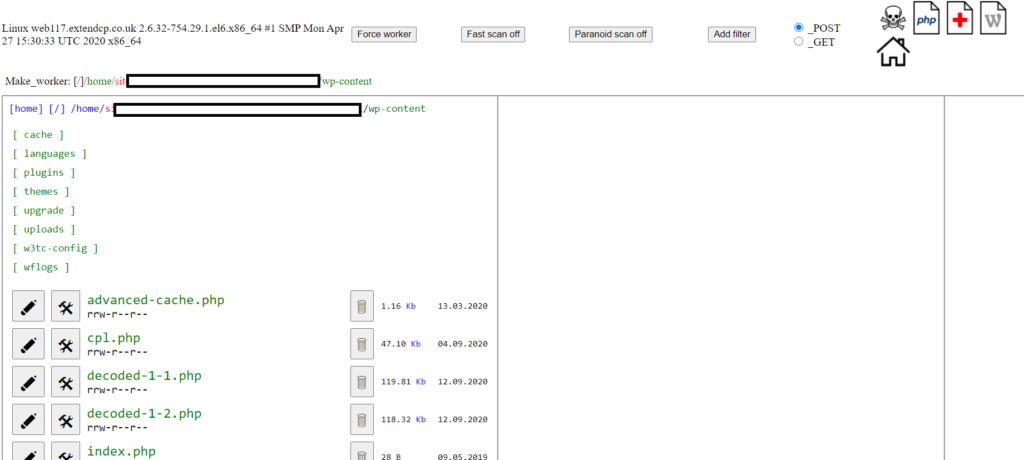
Throughout our diagnosis of the infected server, a deep search among all files outside of the WordPress installation presented some obscure PHP files such as cpl.php.
When publicly viewing cpl.php, the page showed an md5 hash of the user agent that connected with a remaining white space. After reviewing the page by analysing the server side code, an initial IF statement appeared:
If the user agent's md5 hashed was not equal to 0b08bd98d279b88859b628cd8c061ae0 then die (end the page).
if('11c5b718af2cea1de5bfb3bd8c98db2e' !== md5($_SERVER['HTTP_USER_AGENT'])){die('0b08bd98d279b88859b628cd8c061ae0');}
After removing the IF statement, we started to see what was truely behind the intent of this rogue PHP file...a backdoor. The backdoor gave the hacker complete access to the whole server; allowing the user to add, update ore remove any files at will.
My site was hacked, what do I do?
It is paramount to fix the hack as soon as possible, let us explain why for several reasons. Rushax have just had a client come to us with this issue. Their primary source of marketing is via the popular PPC routes of Google Ads. If Google Ads see's the malicious intent behind the infected website, Google will ban their PPC ads from running; equating to lost revenue for the business.
To make matters worse, certain web hosting companies if found will remove or suspend the web hosting completely.
When a website has become infected with malicious intent, assume the worst to ensure we correctly overcome the issue. Otherwise this could lead to reinfection at a later date with backdoors being installed or passwords/credentials being swiped. That means we have to assume access has been compromised for the following:
- WordPress admin users
- FTP/SFTP users
- Database users (including root)
- cPanel area
- Domain name email addresses
Previous studies such as the 2018 Global Password Security Report show a staggering 50 percent of users use the same passwords across different websites. It's important to change these passwords for external sites right away to stop these being compromised too.
Next steps
Take a backup of the website with it's current state. If you have a backup of the website prior to the incident taking place, one option is to change all credentials, delete everything from the server and re-install the original backup; ensuring all credentials are changed. If a backup isn't present, our recommended advice is to consult a cyber security expert to rectify the malware comprehensively.
Make sure the website isn't infected as the average length of time businesses are unaware of being infected is 6 months.
If you require an expert cyber security expert to fix your hacked website, speak to Rushax today to see how we can help offer a fast and effective solution.
Website Design Services
Get a free web design quote by contacting us today.
Get My Free Web Design QuoteRelated Blogs

10 Most Common Phishing Emails to Watch Out For
Phishing emails are everywhere these days, and they’re one of the easiest ways cybercriminals trick people into giving up sensitive […]

What is ISO 9001?
ISO 9001 is a globally recognised standard for quality management systems (QMS). It provides organisations with a framework to consistently […]

How Much Does SSL Certificates (HTTPS) Cost?
SSL (Secure Socket Layer) certificates have become a necessity for any website that collects user data or offers any kind […]