WP File Manager Plugin, a free WordPress plugin available on the WordPress plugin directory, became the latest victim in a series of ongoing hacking attacks. The purpose of the plugin is to manage files throughout your server that you may not previously would have been able to edit or access solely from your WordPress installation.
A key examples where the WP File Manager really comes in handy is if you require uploading a HTML verification file to your server in order to verify your own domain.
WP File Manager was a huge hit among the WordPress community and as such was installed by over 700,000 websites according to WordPress' plugin repository.
From the subsequent attacks, the plugin has suffered around a third of all its previous installations; reducing the total installations to just under 500,000 with more uninstalls likely to occur during the coming days, weeks and months.
The popular WordPress plugin WP File Manager was hacked by a zero day exploit that installed a script on the website to show ads to website traffic of infected websites in order to generate profit for the malicious creator.
From a security aspect, what concerns us most is the amount of native WordPress files that the virus looks for and exploits including the standard plugin Hello Dolly and WordPress's configuration file, wp-config.php.
The system also performed a series of requests to external websites to download and extract various .zip folders depending on which WordPress installation was active.

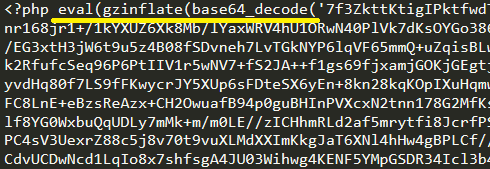
The coding languages used throughout this attack consisted of a mixture of JavaScript and PHP. The malicious code used a combination of encryption techniques to hide the server from detecting malicious code including:
Throughout our diagnosis of the infected server, a deep search among all files outside of the WordPress installation presented some obscure PHP files such as cpl.php.
When publicly viewing cpl.php, the page showed an md5 hash of the user agent that connected with a remaining white space. After reviewing the page by analysing the server side code, an initial IF statement appeared:
If the user agent's md5 hashed was not equal to 0b08bd98d279b88859b628cd8c061ae0 then die (end the page).
if('11c5b718af2cea1de5bfb3bd8c98db2e' !== md5($_SERVER['HTTP_USER_AGENT'])){die('0b08bd98d279b88859b628cd8c061ae0');}
After removing the IF statement, we started to see what was truely behind the intent of this rogue PHP file...a backdoor. The backdoor gave the hacker complete access to the whole server; allowing the user to add, update ore remove any files at will.
It is paramount to fix the hack as soon as possible, let us explain why for several reasons. Rushax have just had a client come to us with this issue. Their primary source of marketing is via the popular PPC routes of Google Ads. If Google Ads see's the malicious intent behind the infected website, Google will ban their PPC ads from running; equating to lost revenue for the business.
To make matters worse, certain web hosting companies if found will remove or suspend the web hosting completely.
When a website has become infected with malicious intent, assume the worst to ensure we correctly overcome the issue. Otherwise this could lead to reinfection at a later date with backdoors being installed or passwords/credentials being swiped. That means we have to assume access has been compromised for the following:
Previous studies such as the 2018 Global Password Security Report show a staggering 50 percent of users use the same passwords across different websites. It's important to change these passwords for external sites right away to stop these being compromised too.
Take a backup of the website with it's current state. If you have a backup of the website prior to the incident taking place, one option is to change all credentials, delete everything from the server and re-install the original backup; ensuring all credentials are changed. If a backup isn't present, our recommended advice is to consult a cyber security expert to rectify the malware comprehensively.
Make sure the website isn't infected as the average length of time businesses are unaware of being infected is 6 months.
If you require an expert cyber security expert to fix your hacked website, speak to Rushax today to see how we can help offer a fast and effective solution.
The number one content management system, WordPress powers over 25% of the internet. Being such a popular platform has led to an opening of various careers path including web designs, web developers, theme developers, graphic designers and plugin developers. The platform has also found itself to have one of the most extensive open sourced marketplaces where free and premium themes are available.
However when looking at a website, it can be hard to determine whether it is powered by the powerhouse that is WordPress. We've put together a five ways that help you identify whether a website is using WordPress.
The source code is the coding language that is used to make the website render as shown by browsers. The source code of all websites can be viewed by right clicking on a page and selecting 'View Source'. Alternatively, you can put into your URL bar the following phrase:
Example: view-source:https://rushax.com
view-source:https://[domainname].com/[page]
Once you can see the code on the browser, look for certain common directories or folder names. You can look for certain phrases by pressing the CTRL + F key (Windows) and CMD + F (Mac) to show a search bar where the following terms can be searched:
If any of these combinations are found within the source code of the website, there is a very high possibility the website is powered by WordPress. For those out there question why, 'very high' has been mentioned; let me explain.
If a website has used a URL of an image from an external website (which uses WordPress) this would pose a false negative. Let's look at some more fail-safe ideas of how we can identify if a website is using WordPress.
The WordPress platform has a standard URL that is used to access the admin area prior to logging in. These can be accessed via two main pathways including:
If we combine either of these combinations with the domain name we will end up with the following two URLs in our browser.
https://[domain-name.com]/wp-admin
https://[domain-name.com]/wp-login.php
If either of these (when replacing 'domainname.com' with the desired domain name) URL's show a login area page, you can bet your bottom dollar the website uses WordPress.
For security purposes though, these are often blocked as automated bots try to login to admin areas for unethical purposes. As a result, login URLs often get changed to different URL paths.
WordPress offers a REST API by default that allows third party applications such as search engine crawlers access to all the information the website holds but in a much more structured format.
By having the information presented in such a manner allows these applications connecting to the website's API to understand specific pieces of information such as the website's title, description, timezone and much more.
The WP JSON or WordPress REST API can be accessed by going to the following URL:
https://[domain-name.com]/wp-json/
If the WP JSON event comes to no avail, or you simply want to know another method of how to find out if a website is using WordPress, then you're in luck!
With every WordPress install, a text (.txt) file gets created that references the WordPress license and its distribution policy. As WordPress is founded on an open-source environment, this means the code is free to use and can be re-distributed and/or modified under the GNU General Public License.
The license text file comes as no surprise as license.txt and can be found at the root of any WordPress install, typically as seen below:
https://[domain-name.com]/license.txt
Replace the 'domain-name.com' with the requested URL of your website choice. If a license page shows up in a standard text file, referring to WordPress at the beginning, you can be sure the website is using WordPress.
Online tools such as Built With are available for free that request a URL. Upon submitting, the website runs through all the technologies that the website uses, including it's Content Management System.
If you found this useful, or have any other ways you know how to find out whether a website uses WordPress, let us know in the comments section below.
Happy WordPress hunting!